Affiliate links on Android Authority may earn us a commission.Learn more.
Study: Some Android OEMs lied about applying security updates (Updated)
June 27, 2025
Update (04/14/18 at 01:50 A.M.):Google has responded to the study, saying they were cooperating with Security Research Labs to shore up the mobile platform’s defenses.
“We would like to thank Karsten Nohl and Jakob Kell for their continued efforts to reinforce the security of the Android ecosystem. We’re working with them to improve their detection mechanisms to account for situations where a device uses an alternate security update instead of the Google suggested security update,” the company noted in an emailed response to questions.

The Mountain View corporation sought to reassure users, saying that security updates were “one of many layers” used to guard Android devices. The company cited Google Play Protect and application sandboxing as two examples of these layers.
“These layers of security — combined with the tremendous diversity of the Android ecosystem — contribute to the researchers’ conclusions that remote exploitation of Android devices remains challenging.”
The response also comes after study co-author Karsten NohltoldAndroid Authoritythat a phone with a few missed updates is still “more secure” than your typical Windows machine.
“…Each phone has a number of security barriers and each missing patch usually affects only one of them. Consumers can take comfort in the thought that an Android phone with a few patch gaps is still more secure than the average Windows computer,” the security researcher elaborated.

Original article:Android brands can definitely do a better job of delivering security updates, but did you know that your phone manufacturer might be hiding patches from you?
That’s according to a two-year-long study by Security Research Labs (SRL), finding a so-called “patch gap,”Wiredreports. The Berlin-based team found that many Android phone manufacturers were far behind on updates, or even lying about the last security update applied to the phone.
“Sometimes these guys just change the date without installing any patches. Probably for marketing reasons, they just set the patch level to almost an arbitrary date, whatever looks best,” Karsten Nohl, Security Research Labs founder, told the publication.
The study found that lesser-known brands were worse than the likes ofGoogleandSamsung. But results could even vary within a brand, as SRL found. The team cited theSamsung J5 2016as being honest about the lack of patches, while the J3 2016 lacked 12 patches (including two deemed “critical”) despite claiming to receive every security update in 2017.
Nohl said that this “deliberate deception” wasn’t as common as vendors simply forgetting to update their devices. Nevertheless, the security company plans to update itsSnoopSnitch appto show users the actual patch status of their handset.
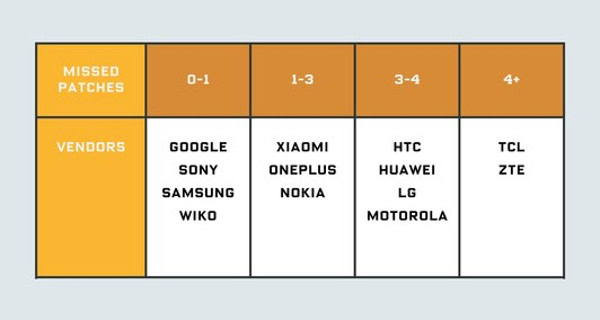
The company also produced a chart (above), showing how many patches a brand was missing on average, despite claiming to be up-to-date. Big winners were Google, Samsung,Sonyand French brand Wiko, whileTCLandZTEbrought up the rear.
There’s far more worrying news for owners ofMediaTek-equipped phones, as SRL found that these devices stealthily skipped 9.7 security updates on average. By comparison, the next highest number was 1.9 skipped patches, by HUAWEI’s HiSilicon.
The research group explained the discrepancy by sayingbudget phonesare more likely to jump over security updates and use cheap chips.Wiredadds that flaws could be found in mobile chips, with manufacturers dependent on the silicon makers to provide these fixes. So even if a company wants to update their phone with a patch, they can’t do much if the chipmaker doesn’t help out.
Nohl told the publication that hackers still have a challenge on their hands, owing to Google’s existingsecurity measures. “Even if you miss certain patches, chances are they’re not aligned in a certain way that allows you to exploit them.”
The results are undoubtedly a cause for concern, but Nohl reckons cyber-criminals will “most likely” stick to social engineering techniques, such as dodgy apps on thePlay Store.
We’ve contacted Nohl, Google, MediaTek, ZTE, and TCL and will update the article if we receive a response.
Thank you for being part of our community. Read ourComment Policybefore posting.